Spoofing occurs when a scammer poses as a trusted source to obtain access to your identity or assets. Spoofers perform various spoofing attacks so they can steal personal information, money, or infect your device with malware.
Using any form of online communication, scammers use spoofing to try to steal your personal information. Read more to learn about how spoofing happens, the different types of spoofing attacks, how to detect it, and how to prevent it from happening to you.
Spoofing Definition
When a scammer disguises themselves as a trusted source to trick users into sharing private data, it’s known as spoofing. This type of scam happens through websites, emails, phone calls, texts, IP addresses and servers. Generally, scammers make a slight change to a trusted URL or email address to fool users with a simple glance.
For example, say you regularly receive emails from Amazon.com. A spoofer may disguise an email by changing the email address to “Amaz0n.com” to trick you into sharing information with that address.
How Does Spoofing Work?
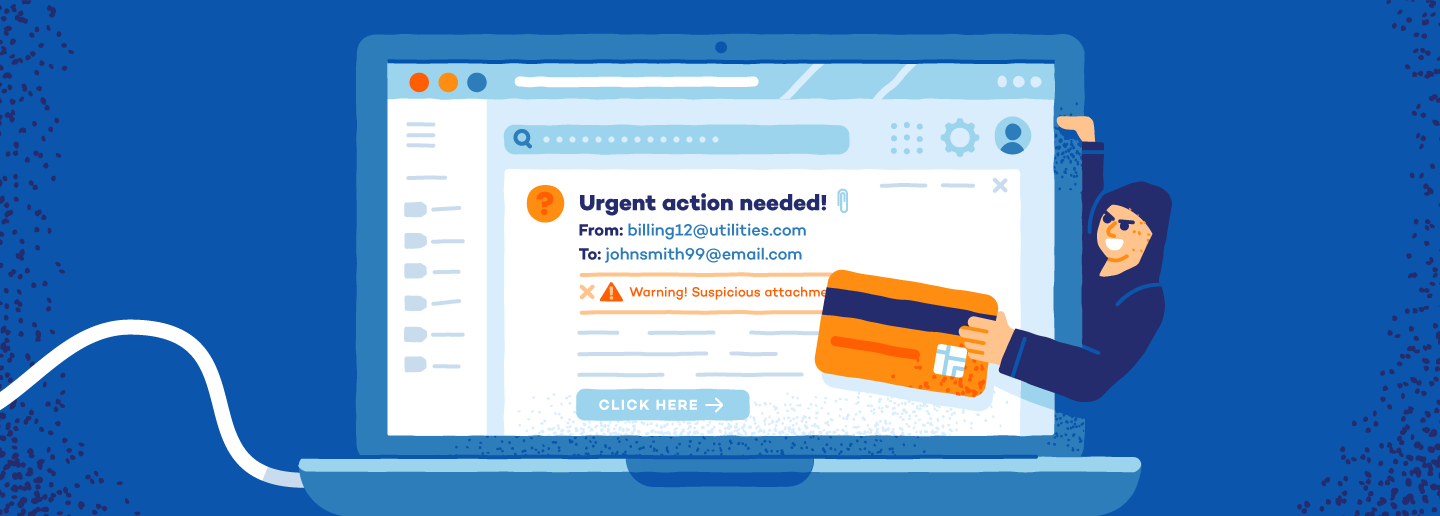
The origin of “spoofing” dates back to the 1800s and refers to any act of trickery or deception. In modern times, spoofing now refers to a type of cybercrime that involves scammers disguising their identity to trick unsuspecting individuals.
Scammers target a variety of online communication channels and the act requires varying levels of technical expertise. Every spoofing attack also employs a certain degree of social engineering.
Social engineering involves being able to effectively trick your target into giving out their personal information. Scammers use it to manipulate human emotions, such as greed, fear, and naiveté to scam important data from their victims.
The grandchildren scam is a typical example of a social engineering scam. In this scam, the scammer pretends to be a member of the target’s family that is in trouble and asks them to send money as soon as possible.
This type of scam plays on a victim’s fear and concern for their family to get victims to share information or send money. The most common targets of this scam are older adults who are less tech-savvy and not aware of the warning signs.
10 Examples of Spoofing
Spoofing comes in many forms, and it’s important to be aware of the different attacks that you may encounter. Below are some common examples of different types of spoofing:

1. Caller ID Spoofing
Caller identification (Caller ID) is a useful tool that allows you to screen the identity of whoever is calling. Scammers can take advantage of this through caller ID spoofing, which involves a scammer using fake information to alter the caller ID.
Using caller ID spoofing makes it impossible for a number to be blocked, so it’s common for phone scammers to use Caller ID spoofing to conceal their real identity. Additionally, a scammer might replicate your area code on the call to make it appear as a local number.
Most scammers use a VoIP (Voice over Internet Protocol) to perform caller ID spoofing. VoIP helps scammers create a realistic phone number and caller ID name. When someone answers the phone, the scammer will try to deceive them into revealing personal information.
2. Website Spoofing
If a scammer makes a dangerous website look trustworthy, usually with legitimate-looking colors and logos, this is known as website spoofing. The purpose is to make a phishing or malicious site look safe, so that people click on it and share their information.
Typically, the copycat site’s URL address will be similar enough to a legitimate site so it looks real upon first glance.
3. Email Spoofing
Another common example of a spoof attack is email spoofing. This happens when a scammer sends an email with a fake sender address in an attempt to infect your device with malware. These fake email addresses typically mimic the address of someone you know, like a relative or a colleague.
Scammers do this by using alternative numbers or letters to create an address similar to the original or by disguising the ‘from’ field as the real email address of a personal connection. This disguised sender address usually lowers your guard and makes it so that you’re more likely to send the recipient funds or personal information.
4. IP Spoofing
IP spoofing occurs when a scammer hides their location when they send a request for data online. Scammers can also alter the IP address so that it impersonates another computer. They do this to trick your device into thinking the information being sent is trustworthy, so it will allow malicious content to pass through.
5. DNS Server Spoofing
Domain Name System (DNS) spoofing sends traffic to different IP addresses, and is often used to bring visitors to malicious websites. Scammers achieve this by replacing the IP addresses stored in the DNS server with the malicious addresses they want you to use.
Because it alters your stored data for malicious purposes, DNS spoofing is also known as cache poisoning.
6. ARP Spoofing
Address Resolution Protocol (ARP) spoofing is frequently used to modify or steal data for in-session hijacking. It’s also referred to as ARP poisoning or ARP cache poisoning. Scammers usually do this by linking their media access control to an IP address so they can intercept data originally intended for someone else.
7. Text Message Spoofing
Did you know that even text messages can be spoofed using another phone number? Text message spoofing refers to when a scammer sends a text, but covers up their identity using an alphanumeric sender ID.
The text messages usually include links to malware downloads or phishing sites. Be sure to brush up on good mobile security tips so that you don’t unknowingly compromise the data on your phone.
8. GPS Spoofing
Scammers perform GPS spoofing by broadcasting false signals to deceive GPS receivers. These signals generally resemble real life signals. This allows scammers to pretend they’re in a different location when they’re actually in another.
This spoofing attack is typically used to hack a car GPS so that scammers send you to the wrong location. GPS spoofing is even used to interfere with the GPS signals of aircrafts, buildings, and ships. Mobile apps that use GPS data are also a target and make devices like your smartphone vulnerable.
9. Man-in-the-middle (MitM) Attack
A Man-in-the-middle (MitM) attack refers to when someone hacks a WiFi network to intercept web traffic between two parties. It also includes when a scammer creates a duplicate fraudulent network in that location for the same purpose.
If the attack is successful, scammers will have the ability to reroute sensitive information, such as logins or credit card numbers, to themselves. They can then use this information for malicious purposes.
10. Extension Spoofing
Extension allows scammers to disguise malware in extension folders. Files are usually renamed as a text document (e.g., “filename.txt.exe”) and have malware hidden inside. When a user opens the text file, they unknowingly run a malicious program.
How to Know If You’re Being Spoofed

If you suspect you’re being spoofed, be aware of these indicators from the most common types of spoofing:
Email Spoofing
- Pay attention to the sender’s address: If you’re unsure whether or not the email you’ve received is legitimate, double-check the address. Scammers will often create ones that are similar. If it’s a suspicious email but from the exact sender’s email address, contact the sender to confirm it’s legitimate.
- Be wary of attachments: Be cautious when it comes to attachments from an unknown sender — or if it’s from a known sender and the contents look suspicious. When in doubt, don’t open these attachments as they may contain harmful viruses.
- Watch out for poor grammar: If the email contains a lot of typos or grammatical errors, it’s a signal that it may be dangerous.
- Do some research: Find the sender’s contact information online and get a hold of them directly to see if the email is real. Also, search the contents of the email via Google if it seems suspicious — if the contents sound too good to be true, it usually is and is likely indicative of a scam email.
Website Spoofing
- Check the address bar: A spoofed website will most likely not be secured. To check this, look at the address bar for an “s” at the end of https://. This “s” stands for “secure” meaning the site is encrypted and protected from cybercriminals. If a site does not have this, it doesn’t automatically mean it’s spoofed, so make sure to check for additional signs.
- Try a password manager: Softwares used to autofill login credentials don’t work on spoofed websites. If the software doesn’t automatically fill out the password and username fields, it could be a sign that the website is spoofed.
- No lock symbol: Websites that are legitimate have a lock symbol or green bar to the left of the website URL address indicating a secure website.
Caller ID Spoofing
- You get calls from unknown numbers: Consistent calls from an unknown number are usually spoofed — don’t answer or hang up immediately.
- You’re getting responses: If you’re getting responses to calls or texts that you never initiated, that could be a sign that your number has been spoofed. For example, you may get text messages from people asking who you are or that you stop bothering them.
- Caller ID says “911”: Spoofed caller IDs often show up as “911 Emergency” instead of the spoofer’s real phone number.
How to Prevent Spoofing Attacks

There are many things you can do to protect yourself against spoofing attacks. Stay one step ahead of scammers with these helpful do’s and don’ts:
Dos
- Turn on your spam filter: This prevents most spoofed emails from even coming into your email inbox.
- Read messages closely: Spoof attacks usually contain poor grammar or unnatural sentence structure. If you see this, it’s a sign that the request is not safe. Always double-check that the URL address of a website or the sender’s email address is correct before sending sensitive information.
- Confirm the source: If you receive communication that seems suspicious, it’s best to reach out to the sender and confirm that the call or email you received is legitimate.
- Check the URL before clicking: If you’re suspicious about a link, use your mouse to hover over the link. A URL address will pop up in the bottom left corner of your window, and you can check out where the link will take you before you click it.
- Use two-factor authentication: Using two-factor authentication adds another layer of security against spoofing attacks to your devices. It’s important to note that it is not completely foolproof, so be sure to pair it with good cybersecurity habits as well.
- Install cybersecurity software: Investing in cybersecurity software is a great way to protect yourself from cybercriminals online. If you suspect that you’re being spoofed, download malware removal or antivirus software to protect your devices from malicious threats or viruses.
Don’ts
- Don’t download or click unfamiliar links or attachments: If a link or attachment looks questionable, don’t click on it. If they’re from a scammer, it likely contains malware or other viruses that are dangerous for your computer.
- Don’t answer calls or emails from unknown senders: If you don’t recognize the sender, don’t respond to the call or email. By not communicating with a potential scammer, you avoid revealing your personal information.
- Don’t disclose sensitive information: Avoid sharing personal information, like your address, bank account, or social security number. If you need to provide this information, take extra steps to confirm that it’s a trusted source.
- Don’t use the same password: Many people use weak passwords that scammers can easily guess. Create strong passwords and update them often to prevent scammers from getting a hold of one. Also, never use the same password for every login.
If you think you’ve been spoofed, you can file a complaint at the FCC’s Consumer Complaint Center. You can also contact your local police department if you’ve lost money due to spoofing.
Be sure to check out our antivirus software to secure your digital life today and protect yourself against spoofing.





